If you have been following the coverage of Zoom’s data and virtual meeting security struggles you may have stumbled across the term end-to-end encryption (E2EE), an important security feature of many (though, not all) instant messaging and conferencing apps.
Encryption is an algorithm that ensures data can only be read by specific recipients, and not accessed by random people, or other algorithms.
Your digital credit card and banking information are encrypted to keep it safe when you use online banking, for example.
Summary
End-to-End Encryption is the strongest form of encryption available. Platforms we are able to offer your business, like Cisco WebEx, offer E2E Encryption as an option but also adhere to very strong industry-standard privacy and encryption standards.
Zoom Conferencing implemented a custom version of encryption which was found by Citizen Lab, a UK based security firm, to be extremely weak and could put your sensitive business data and communications at risk.
If it wasn’t encrypted, someone could pull it off a Wi-Fi network with relative ease, making the entire concept of the Internet, let alone online financial transactions, a very risky proposition.
Fraud and identity theft would be rampant. Encryption is a basic prerequisite for the use of the Internet.
According to Berty Technologies, a peer-to-peer messaging app, encryption can be likened to a kind of digital envelope that prevents the data placed in this envelope from being read, with the exception of senders and recipients.
There are two basic types of encryption.
One is encryption in transit, the kind where transmitted data between a device – such as your mobile phone – and a server – such as your internet provider – are secured along the way. But the service provider has access to the unencrypted data, and you have little choice but to trust that your service provider will protect it.
The second form is end-to-end encryption. With this type of encryption, data are encrypted between you all the way through to the person you are communicating with, meaning that intermediaries such as your service provider cannot access it; only the sender and the recipient can.
For this to work, two unique codes (or keys) need to be embedded with the data, one to encrypt the data and a second to “decrypt.” In other words, if the data is accessed along the way, it cannot be opened by anyone (or anything) but the user for whom it was destined.
This is why so many government agencies, institutions and businesses around the world abandoned the popular Zoom app as quickly as they adopted it.
It may be hard to remember that Zoom was not a well-known virtual conference option in the enterprise space only a few short weeks ago.
Then, seemingly overnight, due to the COVID-19 pandemic and the global move to work from home, it became the go-to platform to hold lessons, business meetings, and sensitive discussions.
The number of daily users exploding from 10 million to 200 million from December to March.
Zoom has been aggressively marketing its services, and because so many users found themselves at home needing to quickly establish communications channels, they began setting up easy-to-use Zoom accounts.
This kind of thing would generally no pass muster with most self-respecting IT departments, but we all know how quickly things have moved these past few weeks. So, clearly important procurement processes were short-circuited to get people up and running from home.
As the service’s popularity has surged, Zoom security has come under close scrutiny and exposed it for a variety of issues including the phenomenon known as Zoombombing, the unwanted disruption of video conference calls by posting inappropriate materials, as well as questions about its claims to feature E2EE.
On March 31, the Intercept reported that Zoom, in fact, employs encryption in transit, which means that user information can be accessed at the server level. For individual users, this is not a big deal.
Google Hangouts, cell phone and Skype calls, for example, are not E2EE and it is unlikely the average person would need this level of security. But when you consider classified government information or corporate strategies, you want to use a more secure platform. The threat was further highlighted when it was revealed that Zoom data was “mistakenly” routing some user data through servers in China.
Zoom has pledged to fix security and privacy issues, and some features have already been rolled out including updated passcode protocols and the removal of code that sent user data to Facebook. But many issues, including E2EE, have yet to be addressed.
So, what are your options if you are looking for a conferencing platform that will meet your business’s security needs.
Probably the best platforms when it comes to overall security are Cisco Webex and Microsoft Teams, which both effectively serve businesses, educational and health institutions, and government agencies worldwide.
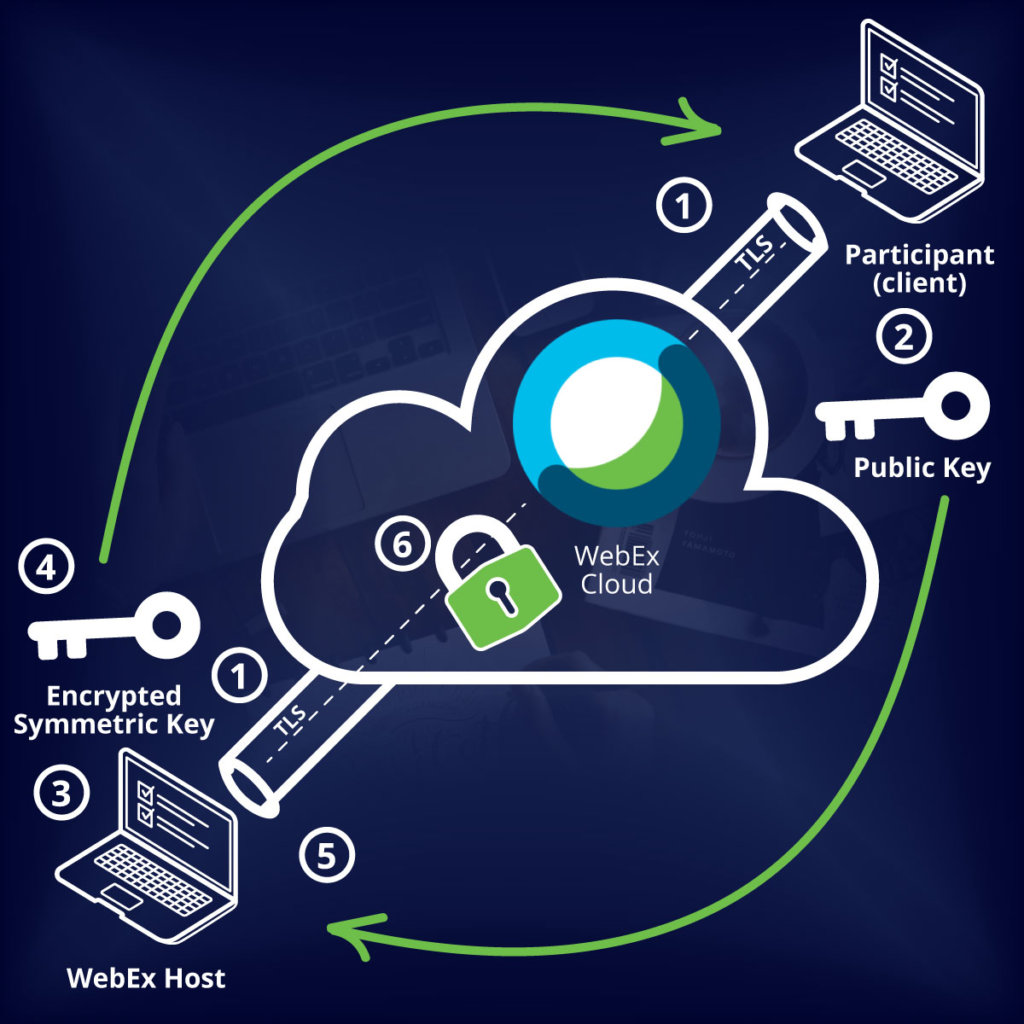
Webex has a reputation for maintaining robust cybersecurity and offers a shopping list of security features including the option of establishing E2EE in media streams for businesses that require this added layer of data security.
While Teams’ E2EE status is vague, it does have an internal rating system for the security of its products, and has designated Teams to be Tier-D compliant, which means that it can adhere to the strictest government and industry security standards and legal requirements.
If you want to know more, Momentum Conferencing offers a range of collaboration tools including Cisco Webex and Microsoft Teams. Our team takes pride in working with clients to find the right collaboration tools to help businesses remain productive. Let us know how we can help assure your business stays on track.
We are standing by and ready to assist @ 1-888-551-5925 x2 or clientservices@momentumconferencing.com.


